
Business Impact Analysis (BIA)

Management Summary
Business Impact Analysis (BIA) is an essential component of a Business Continuity Management System (BCMS) and analyses the impact of disruptions on business continuity as an organization, company or authority in order to strengthen resilience. In this article, BIA is first described, then the steps "preparation, implementation and evaluation" are explained in a practical way and finally the experiences are explained as lessons & learned. This article is fundamentally based on BSI Standard 200-4 "Business Continuity Management". Reading time 10 minutes. | Author: Ayhan Dagli
What is Business Impact Analysis (BIA)?
Business impact analysis (BIA) is an important core element in ensuring business continuity. During a BIA, companies examine which business processes are time-critical and at what point their failures have unacceptable effects. BIA helps to strengthen a company's resilience and ensures that critical business processes can continue even in emergency situations.
The BIA focuses on the potential effects of a business process failure, not on its causes or probabilities. Whether a business process fails due to the unavailability of the building due to fire, flooding, power failure, an essential IT application or the service provider is therefore irrelevant for the BIA and the identification of time-critical business processes. Furthermore, a BIA not only assesses the impact on the company, but also how the potential damage develops over time.
The result of the BIA shows which business processes and resources are time-critical and therefore need to be taken into account in the subsequent BCM steps, particularly in the target/actual comparison and in business continuation and restart plans.
An overview of the BIA steps is shown below.

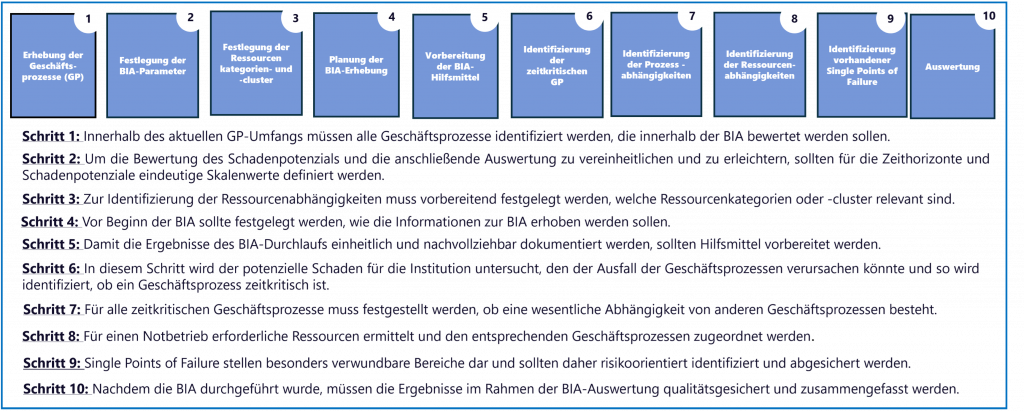
Preparation of the BIA
A structured preparation phase ensures that a BIA is carried out successfully and smoothly. The BCB determines the methodology and procedure, but can delegate all or part of the preparatory activities to other roles in BCM.
Survey of business processes
First, the business processes that are to be evaluated within the BIA are identified. Companies may be able to draw on existing overviews of their business processes for this purpose. The process map can be a helpful tool for this. If there is no current overview of the business processes and their dependencies, this must be collected or updated as part of the BIA.
Synergy potential: If an ISMS in accordance with BSI standard 200-2 or ISO standard 27001 is in place, the business processes identified there can be used as a basis.
Definition of the BIA parameters and time horizons under consideration
The number and subdivision of time horizons should be chosen in a comprehensible manner and be based on the company's circumstances. It is therefore advisable to define five to eight time horizons, e.g. 24 hours, 3 days, 7 days, 14 days and 30 days.
In addition to the time horizons, the damage potential is also determined, which is derived from the damage scenarios and the damage categories. [e.g.: 1 (low), 2 (medium), 3 (high), 4 (very high)] is derived. As a minimum, the following damage scenarios should be considered within the BIA:
- Impairment of the fulfillment of tasks
- Violation of laws, regulations and contracts
- Negative internal and external impact (damage to image)
- Financial impact
- Impairment of personal integrity
The unacceptability level is another parameter and defines the damage potential at which the effects of a failure can no longer be tolerated by the company.
Synergy potential: If an ISMS in accordance with BSI Standard 200-2 already exists, the damage scenarios and damage categories defined in the protection requirements assessment can be used as a basis. This promotes the comparability of results between the BCMS and ISMS.
Definition of resource categories and clusters
In principle, a company needs electricity, water supply, air conditioning, etc. for its business operations. However, it is not practical to collect these resources for each individual business process, as they are required to maintain the entire business operations.
The resources that are specifically required for a business process must therefore be determined in the BIA. These resources can be divided into different resource categories, e.g. IT, personnel, infrastructure and services. It is advisable to adapt the number and description of the resource categories to the needs of the company. On the other hand, there can sometimes be a large number of individual resources within certain resource categories, e.g. IT. It makes sense to group these resources into clusters. The most common example of a cluster is the workplace.
Synergy potential: If an ISMS in accordance with BSI Standard 200-2 is in place, information from the structural analysis can be used for the designation of various resources or workstation definitions and room lists can often be derived from the building management.
Planning the BIA survey
Before the BIA begins, it should be determined how the information for the BIA is to be collected. Various formats are available for this, e.g. self-disclosure, individual interviews, workshops or a mixed format. Workshops can be beneficial for first-time BIAs so that those responsible can have a common understanding.
Preparation of the BIA aids
Various tools can be prepared to document the results of the BIA run in a standardized and comprehensible manner or to inform the person responsible or to collect information from them. Various tools have been made available free of charge as templates on the BSI website.
In practice, the "BIA presentation template" and "BIA evaluation sheet" tools in particular have been used effectively. However, experience has shown that it is advisable to collect the data using separate tables/aids and to record them step by step in the evaluation sheet. The additional tools created for this purpose, which are derived from BSI Standard 200-4, are as follows:
- Assessment of the damage potential (200-4; tables 18, 19 and 20; pages 178, 179 and 180)
- Definition of the MTPD of the business processes (200-4; Table 21; page 181)
- Justification of the damage potential (200-4; Table 22; page 182)
- Emergency operating level (200-4, Table 23, page 184)
- Definition of the RTO and RPO of the resources of the time-critical business processes (200-4, Tables 24 and 26; pages 189 and 191)
- Number of workstations or personnel in emergency operation. (200-4; Table 25, page 190)
Implementation of the BIA
Depending on the organizational planning, the BIA is carried out either in the form of workshops with several people or independently by the responsible contact persons.
Identification of time-critical business processes
The identification of time-critical business processes examines the potential damage to the company that the failure of business processes could cause.
Assessment of the loss potential of business processes
The damage potential of each business process in the GP scope must be assessed over various time horizons using the damage scenarios and damage categories already defined. This should be carried out by the contact persons for the business processes. If necessary, other experts can be involved to assess the damage potential in specialist areas. The following key question can be asked for the assessment.
Key question: If the business process "ABC, DEF etc." fails, what potential damage [1 (low), 2 (medium), 3 (high), 4 (very high)] can be expected in the event of a failure up to [24 hours, 3 days, 7 days, 14 days, 30 days]?
Determination of the MTPD / MTA or RTO
To determine the MTPD (Maximum Tolerable Period of Disruption) / MTA (Maximum Tolerable Downtime) of a business process, the shortest time horizon should be selected at which the unsustainability level is reached, as the failure can no longer be tolerated after this period. RTO (Recovery Time Objective) is also defined for time-critical business processes. This period should be shorter than MTPD / MTA.
Determination of the emergency operating level
In order to be able to determine mandatory process and resource dependencies, the level of emergency operation that a time-critical business process should achieve must be defined in advance. For this purpose, it is sufficient to provide a brief description of which activities of the business process are to be maintained within the emergency operation and which activities can be postponed (prioritization). Depending on the task or business purpose, it is also possible to specify the emergency operation level as a percentage.



Identification of process dependencies
The business processes can fail either due to the failure of resources or the unavailability of required business processes. It must therefore be determined for all time-critical business processes whether there is an indispensable dependency on other business processes for emergency operation. This dependency can result from upstream or downstream activities, which may also build on each other in parallel.
Identification of resource dependencies
For all time-critical business processes, the resources required for emergency operation must be determined and assigned to the corresponding business processes. Experience shows that not every resource that is used by a business process in normal operation is automatically required in emergency operation. The resources should therefore be checked in this phase and, if necessary, omitted or supplemented.
RTO of the required resources
In addition to the RTO of the business processes, the RTO of the required resources must also be determined. If several business processes use the same resources, the smallest RTO for this resource must be selected. Tools such as the BIA evaluation sheet from the BSI offer this option.
Resource requirements depending on the duration of the emergency operation
For many resource categories (personnel and workstations, but also machines or work equipment), the number of resources required can change with the duration of the emergency operation. For these resource categories, it is therefore advisable to determine the number of resources required over the defined time horizons during emergency operation. This allows the increasing volume of work and the remaining capacity to be taken into account and the workload to be distributed appropriately.
RPO of information-based resources
For information-based resource categories, such as information and IT (data), the RPO (recovery point objective / maximum tolerable data loss) must also be determined. The data backup interval of normal operation is often sufficient as the RPO.
Identification of existing single points of failure (SPoFs)
If many time-critical business processes require a single resource, this poses an increased risk of business interruption. Such resources are usually referred to as single points of failure. These should be identified and secured in a risk-oriented manner.
Evaluation of the BIA
After the BIA has been carried out, the results must be quality assured and summarized. In order to ensure a uniformly high level of quality of the BIA results, the results must be checked for completeness, correctness and comprehensibility. It is important to check whether all the necessary information has been collected, whether the damage analysis has been carried out correctly in formal terms and whether the reasons for the damage analysis appear plausible.
For this purpose, the individual results should be summarized in an overview. The overview should include at least the following content:
- Overview of time-critical business processes and associated contact persons,
- Overview of process dependencies and
- Overview of dependent resources and their RTO or RPO.
Lessons & Learned of a BIA implementation
- The BIA was basically prepared and carried out in accordance with BSI Standard 200-4, but the approaches of different norms / standards were also taken into account.
- As a synergy effect, the business processes and resources from the information security management system (ISMS), which was implemented in parallel with BCMS, were used as a basis.
- The BIA parameters proposed in BSI Standard 200-4 were evaluated and accepted by the company management. In addition, the damage categories and scenarios were coordinated with those in the ISMS protection requirements assessment.
- The BSI tool "Presentation to explain the BIA" was adapted to the company's requirements and used effectively during the BIA.
- The "BIA evaluation sheet" was used as an aid / tool both for carrying out and evaluating the BIA. Additional separate tables / tools were created for this purpose and used to collect the data (so to speak: aid to the aid).
- The importance of the support and cooperation of the management of the companies or organizational units was noted so that the BIA can be prepared on time, completely and correctly.
- Various formats (mixed format) were used in the preparation and implementation, e.g. self-disclosure by the process owner, questionnaires, individual interviews with various people (e.g. heads of organizational units, process owners or other process experts who can provide information) or workshops with several people.
- When assessing the damage potential of a business process, the unfavorable point in time was taken into account, as the failure of this business process could cause a high level of damage, particularly at this point in time, due to the legal requirements.
- When identifying the RTO of the business processes, difficulties arose from time to time, as the difference between RTO (Recovery Time Objective) and RTA (Recovery Time Actual) was not entirely clear to the technical experts. While the RTO is a target value and relevant for planning, the RTA is an actual value that can be determined through tests and exercises or an actual event, such as a cyberattack.
Sources
The following sources were used in the preparation of this article:
- Various aids to BSI Standard 200-4
- BSI Standard 200-4 Business Continuity Management (BCM)