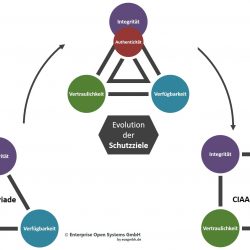
Protection Goals: CIA and CIAA
Protection Goals: CIA and CIAA Management Summary The traditional protection goals of information security are confidentiality, integrity and availability. These three protection goals are often referred to as the CIA triad (owing to the initial letter of the respective goals).Meanwhile, another protection goal has gained in importance. First mentioned by the BSI as a sub-area[…]